The OTOPIQ Platform
Ensure uptime and productivity in complex multi-vendor OT environments
Security and operations teams face different challenges — but share the same risks.
Complex OT environments blend legacy and modern devices, creating gaps in visibility and control that put operations at risk.
Security teams struggle to monitor every PLC, RTU, HMI, and engineering workstation across mixed vendors and with network-only tools.
Operations teams face constant pressure to maintain uptime, safety, and compliance while managing countless assets and contractors.
Without unified visibility and control, internal mistakes, external threats, or unauthorized changes can quickly escalate into major disruptions — impacting production, resilience, and ROI.
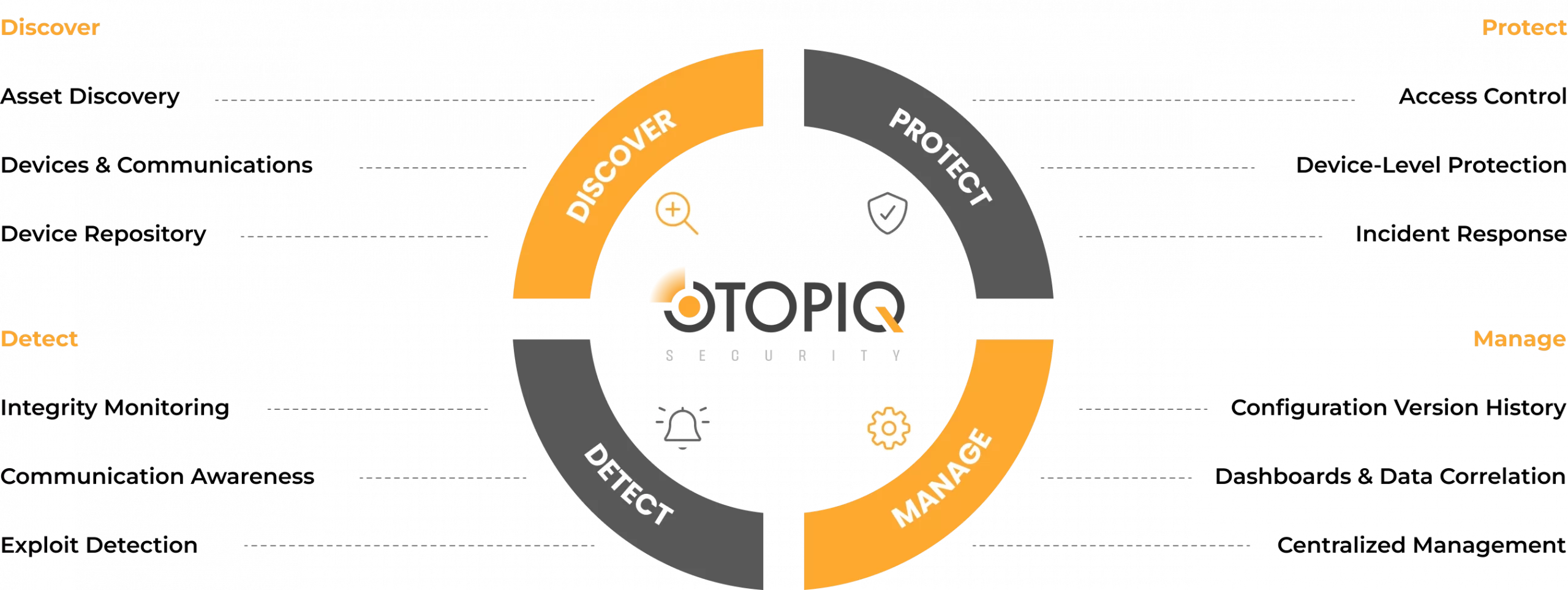
OTOPIQ unifies discovery, protection, detection, and management in one automated platform, securing every Level 1 and 2 OT device — PLCs, RTUs, HMIs, and engineering workstations.
Powered by AI-driven automation, it delivers continuous visibility, zero-trust access control, and instant recovery from unauthorized changes — helping teams prevent disruptions, reduce downtime, and strengthen operational resilience.
- One platform for all devices
Manage and protect every asset, old or new, from a single place - Fast to deploy
No vendor coordination or system changes required - Always protected
Keep every device secure, whether connected, offline, or air-gapped - Zero disruption
Maintain full performance and uptime during deployment and operation - Built for compliance
Simplify audits and meet global regulatory standards
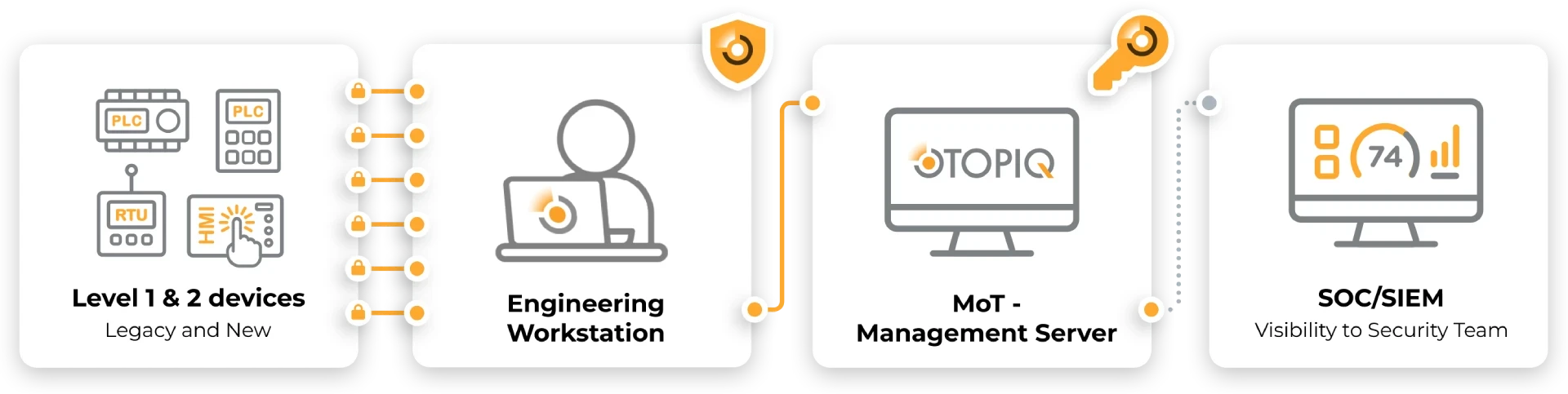


- Centralized Oversight
Single interface for all types of Industrial Control Systems (ICS) - Legacy Modernization
Extends lifespan with consistent, compensating security controls - Standardized Governance
Ensures common policies and visibility across distributed operations

The OTOPIQ Platform provides complete traceability of every action taken within operational environments — showing exactly who did what and when.
Each change, request, and configuration update is authenticated, authorized, and recorded through a single management interface, enabling continuous oversight and accountability.
Audit trails and alerts can be easily exported or integrated with existing SOC, SIEM, and analytics systems to strengthen visibility and compliance.
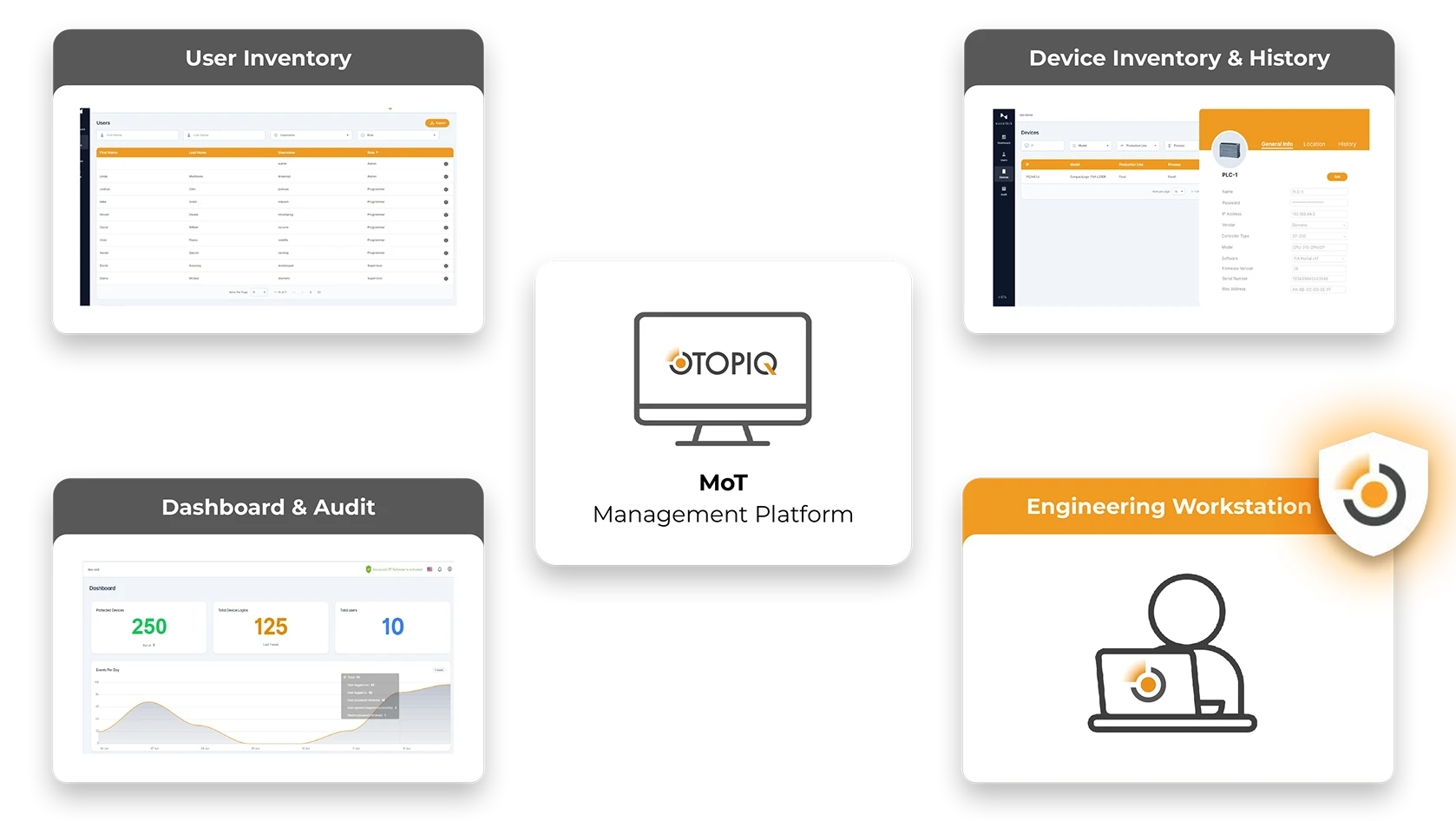
Ensure accountability for every user — internal or external.OTOPIQ authenticates and authorizes all access and changes, enabling secure collaboration between operations, engineering, and security teams.
- Full Accountability – Identity-based authentication and role management
- Complete Traceability – Every change and update tied to both user and device
- Secure Collaboration – Verified access for engineers, contractors, and operators
Compliance
Ensuring Compliance with International Security Standards & Guidelines



